購買憑證 / 續購憑證
憑證是從 namecheap 購買
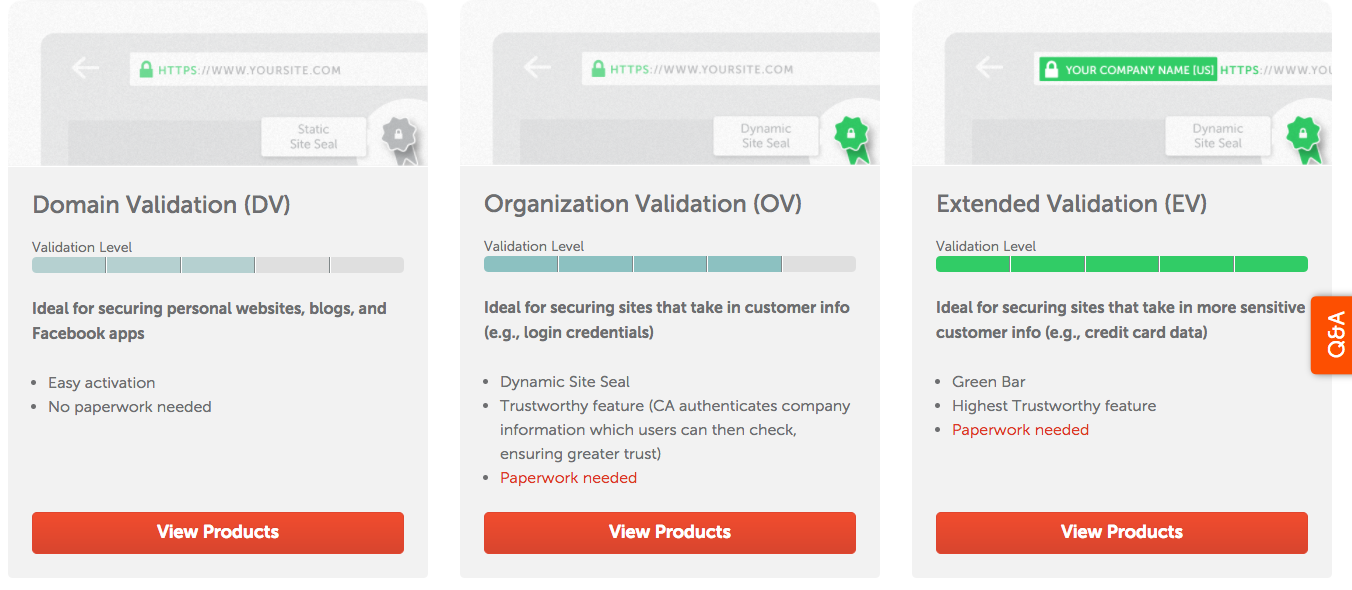
在購買之前可以先了解 level of validation: DV, OV, EV
網頁也有詳細說明
購買的部分,因為太簡單了,就不再贅述
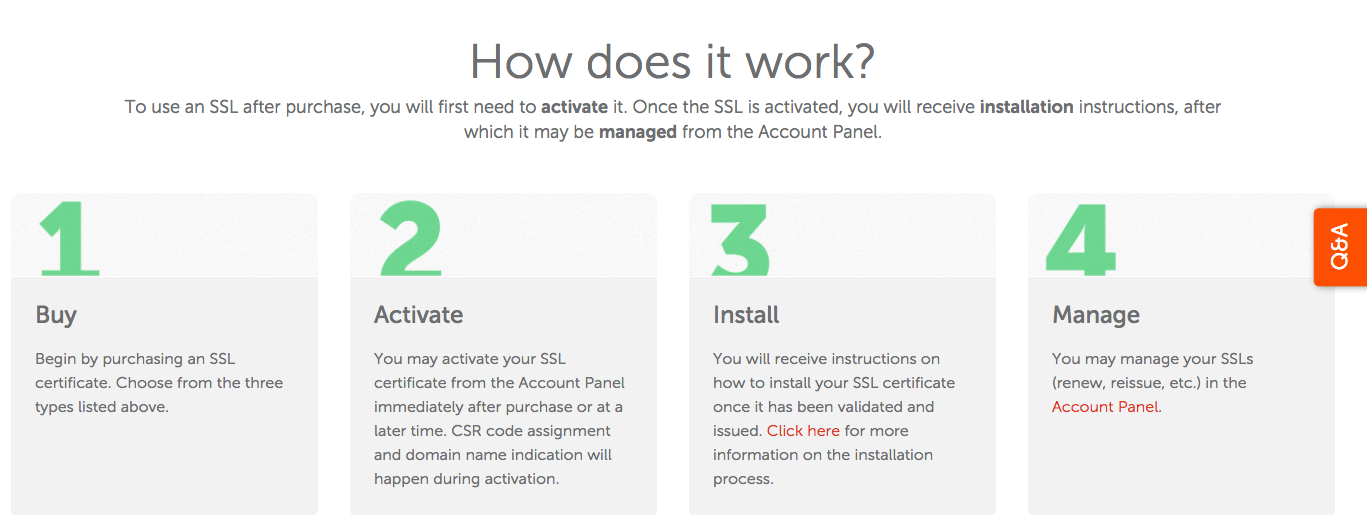
設定憑證
分成四個步驟 CSR -> Validation -> Contacts -> Confirm
四個步驟中,就 CSR 比較複雜,其餘看說明就可以囉!
CSR - Certificate Signing Request
如果是新的網站,就要自己建立一組 private key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ openssl req -new -newkey rsa:2048 -sha256 -nodes -keyout server.key -out server.csr
# 填寫憑證資訊
Country Name (2 letter code) [AU]:TW
State or Province Name (full name) [Some-State]:TAIWAN
Locality Name (eg, city) []:NEW TAIPEI CITY
Organization Name (eg, company) [Internet Widgits Pty Ltd]:DOMAIN LTD
Organizational Unit Name (eg, section) []:
# 網址
# 根據購買certificate 的種類有關
# PremiumSSL Wildcard 多個網址:*.domain.com
Common Name (e.g. server FQDN or YOUR name) []:*.domain.com
# PositiveSSL 單一網址:www.domain.com
Common Name (e.g. server FQDN or YOUR name) []:www.domain.com
Email Address []:service@domain.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
複製 CSR 資訊,貼到 CSR 區塊
1
2
3
4
$ cat server.csr
# -----BEGIN CERTIFICATE REQUEST-----
# ...
# -----END CERTIFICATE REQUEST-----
HTTPS Setting
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
# /etc/nginx/sites-enabled/domain-name-ssl.conf
server {
listen 443 ssl spdy default_server;
server_name domain-name.com;
# SSL configuration
# 根據之前購買的憑證,會寄送domain.crt 檔案到信箱
# 然後把步驟一的 server.key 和 domain.crt 上傳到server /etc/ssl/
ssl on;
ssl_certificate /etc/ssl/domain.crt;
ssl_certificate_key /etc/ssl/domain.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA;
ssl_prefer_server_ciphers on;
# Turn on Passenger
passenger_enabled on;
passenger_ruby /home/apps/.rvm/gems/ruby-2.2.5/wrappers/ruby;
rails_env "production";
location ~* ^/(assets|images)/ {
expires 1y;
add_header Cache-Control "public";
if ($request_filename ~* ^.*?\.(eot|ttf|woff|svg|otf|woff2)$) {
add_header Access-Control-Allow-Origin *;
}
break;
}
}
HTTP
設定請獨立出來,不要與HTTPS 寫在一起,將網址轉到(301)到 https
1
2
3
4
5
6
7
# /etc/nginx/sites-enabled/domain-name.conf
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name _;
return 301 https://$host$request_uri;
}
加強安全性
如果到這一步,表示你之前都已經完成了!(當然..)
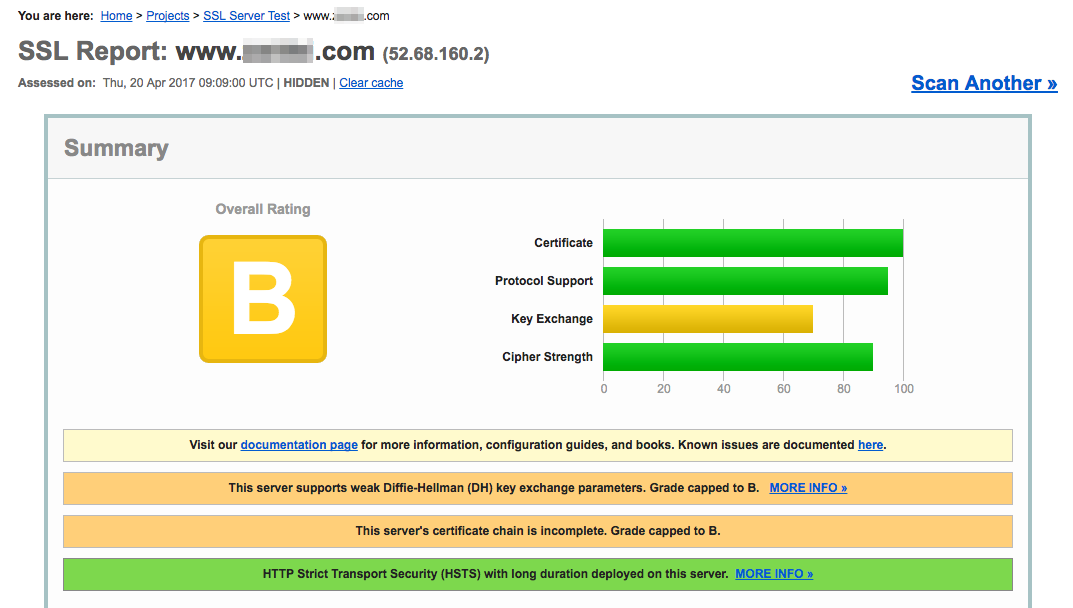
請到 ssl labs 測試網站安全性
沒看錯得到了分數 B !!
感謝網路大神分享文章 用 nginx 建置一個 A+ 等級的 https 網頁伺服器 解決labs 指出需改善的問題
1.This server supports weak Diffie-Hellman (DH) key exchange parameters. Grade capped to B.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# 使用 openssl 命令產升 4096-bit “Strong” Diffie Hellman Group
$ openssl dhparam -out dhparams.pem 4096
# 產生出來的 dhparams.pem 請把它當作你其他的 private key 一樣好好保管
# 安全起見請調整檔案的owner, group以及權限
$ sudo chown www-data:www-data dhparams.pem
$ sudo chmod 400 dhparams.pem
# /etc/nginx/sites-enabled/domain-name-ssl.conf
server {
# ...
ssl_certificate /etc/ssl/domain.crt;
ssl_certificate_key /etc/ssl/domain.key;
+ ssl_dhparam /etc/ssl/dhparams.pem;
# ...
}
# reload config
$ sudo nginx -t
$ sudo service nginx reload
# 測試成功!!但還是拿到Rank B
2.This server’s certificate chain is incomplete
這是因為憑證只有最後簽發的,並未包含中間簽核單位的資訊,導致此問題出現
憑證是跟 Comodo 購買的所以網站上可找到中間簽核單位的憑證
Intermediate #3 申請的憑證 www_domain_com.crt
[Intermediate #2 (SHA-2)] Comodo RSA Domain Validation Secure Server CA (https://goo.gl/pNFYR8 )
[Intermediate #1 (SHA-2)] COMODO RSA Certification Authority (https://goo.gl/b32Q0T )
接著把 #3, #2, #1 照順序組合在一起變成一個檔案
1
2
3
4
5
6
7
8
# /etc/nginx/sites-enabled/domain.conf
server {
# ...
- ssl_certificate /etc/ssl/domain.crt;
+ ssl_certificate /etc/ssl/domain_bundle.crt;
# ...
}
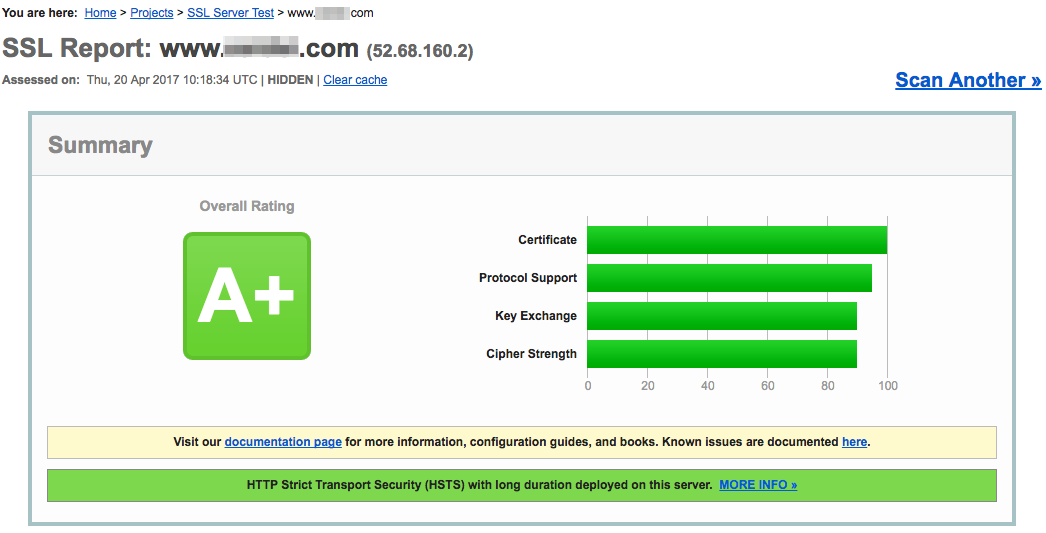
以上問題都調整完之後,再測試一次,終於會得 A+